ACL
In this article:
ACL#
General information#
Access Control Lists (ACLs) act as firewalls at the subnet level. When creating a VPC, a default ACL is also created. It is assigned to each subnet being created and permits all inbound and outbound traffic. The relevant rules are shown in the tables below.
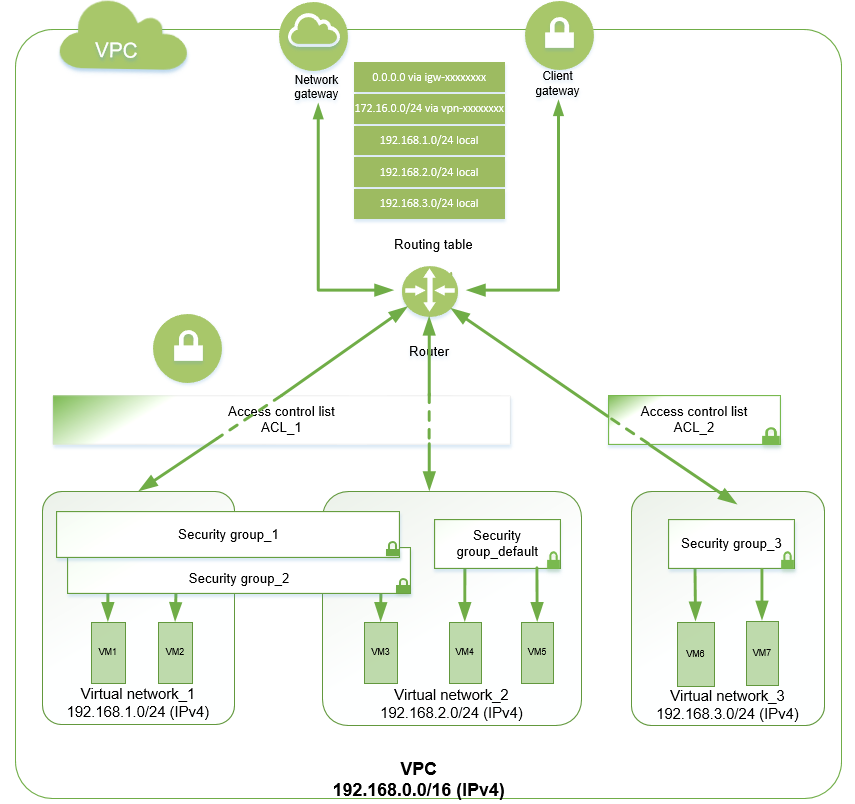
Once a subnet is created, you can associate your access control list with it. The figure shows how ACLs can be associated with subnets and security groups, with network interfaces. For example, you may associate an ACL with several subnets.
Rule number |
Protocol |
CIDR |
Ports |
Action |
|---|---|---|---|---|
100 |
all(-1) |
0.0.0.0/0 |
Allow |
|
32767 |
all(-1) |
0.0.0.0/0 |
Deny |
Rule number |
Protocol |
CIDR |
Ports |
Action |
|---|---|---|---|---|
100 |
all(-1) |
0.0.0.0/0 |
Allow |
|
32767 |
all(-1) |
0.0.0.0/0 |
Deny |
Attention
If the ACL is assigned to a subnet attached to a transit gateway, then outbound ACL rules will not be applied to the traffic coming from the transit gateway.
Operations with ACLs#
Create an ACL#
Go to Virtual machines Security ACL.
Click Create.
In the window that opens, set the following parameters:
Name tag (optional);
VPC in which you want to create an ACL.
If you need to set tags, go to the next step by clicking Add tags. Specify the tag key and value.
After setting all the required parameters, click Create.
The created ACL will contain two rules that prohibit all inbound and outbound traffic, but they will have the lowest priority. Follow the link with the ACL ID to specify your own rules, assign ACL to subnets, and view the list of associated subnets and general information about this ACL.
Associate an ACL with a subnet#
Go to Virtual machines Security ACL.
Select the ACL in the resource table.
Click Associate with subnets.
In the window that opens, select subnets which ACL should be associated with.
Note
To narrow down the ACL search, you can use the VPC selector or search across the resorce table. You can select multiple subnets at once. Only one ACL can be associated with a subnet, but you can always change your choice and associate a different ACL with the subnet.
Note
To associate another ACL with a subnet, just assign it to the subnet.
Click Assign.
This operation can also be performed on the ACL page. To do this, go to the Subnets tab and click Associate with subnets.
If you want to know what subnets are associated with a specific ACL, open the Subnets tab on the ACL page.
Attention
You may associate an ACL with a maximum of 200 subnets in a VPC.
Delete ACL#
Important
Before deleting an ACL, make sure it is not associated with any subnet. If the ACL you are going to delete is associated with a subnet, then first associate another ACL with it.
Go to Virtual machines Security ACL.
In the resource table, select the ACL and click Delete.
In the window that opens, confirm the deletion.
This operation can also be performed on the ACL page. To do this, go to the Information tab and click Delete.
Attention
The default ACL cannot be deleted.
Working with rules#
Each ACL has numbered inbound and outbound rules to permit or prohibit traffic at the subnet level. The rules are applied in order of priority, which depends on the rule number: the lower the number, the higher the priority of the rule and vice versa. We recommend that you first create rules with numbers divisible by 100. Thus, you will avoid problems when adding a rule with an intermediate priority between two existing rules. The maximum rule number is 32766.
Attention
An ACL cannot contain two rules of the same direction with the same number. In addition, you cannot create more than 20 rules in the same direction.
Create a rule#
To add an inbound or outbound rule:
Go to Virtual machines Security ACL.
Find the ACL in the resource table and click its ID to go to the ACL page.
Open the required Inbound rules or Outbound rules tab and click Add.
In the window that opens, set the required parameters:
Rule number.
Rule type.
Protocol — You can set the rule for all protocols or select a specific protocol from the list. If there is no required protocol on the list, select
Other.Protocol number — If the protocol is not on the list, set its number according to IANA.
Port access — For TCP and UDP, specify whether all or specific ports can be accessed.
Ports — If you select access to only some ports, specify a comma-separated list of ports and/or port ranges.
Note
A separate rule will be created for each port or port range in the list.
Grant access — You can grant access from all IP addresses or a specified network.
Network — If you select
From Network, specify the network in CIDR notation.
Once all parameters are set, click Add to create a rule.
Once the addition is confirmed, the subnets, which this ACL is associated with, will filter traffic according to the new security rules.
Modify a rule#
Go to Virtual machines Security ACL.
Find the ACL in the resource table and click its ID to go to the ACL page.
Open the required Inbound Rules or Outbound Rules tab, select the rule to be modified in the resource list, and click Modify.
In the window that opens, you can edit the following parameters:
Rule number.
Rule type.
Protocol — You can set the rule for all protocols or select a specific protocol from the list. If there is no required protocol on the list, select
Other.Protocol number — If the protocol is not on the list, set its number according to IANA.
Port access — For TCP and UDP, specify whether all or specific ports can be accessed.
Ports — If you select access to only some ports, specify a comma-separated list of ports and/or port ranges.
Grant access — You can grant access from all IP addresses or a specified network.
Network — If you select
From Network, specify the network in CIDR notation.
Once the parameters are edited, click Change to save the rule.
Once the changes are confirmed, subnets, which this ACL is associated with, will filter traffic according to the new security rules.
Delete a rule#
You can delete several rules simultaneously.
Go to Virtual machines Security ACL.
Find the ACL in the resource table and click its ID to go to the ACL page.
Open the required Inbound rules or Outbound rules tab, select the rule(s) to be deleted in the resource list, and click Delete.
In the window that opens, confirm the deletion.
Information on the ACL#
For general information about available ACLs, see the ACL subsection. To view all ACLs in the project, select All VPC in the VPC filter. To display ACLs from a particular VPC, select the desired VPC in the filter.
To view detailed information about a particular ACL, go to Virtual machines Security ACL and select the desired ACL. To facilitate the ACL search in the table, select its relevant VPC in the VPC filter or use the table search.
Once you have selected the desired ACL, click its ID. The ACL page will open.
The Information tab displays the main ACL characteristics:
ACL name (Name tag);
whether it is a default ACL (Yes/No);
VPC where the ACL was created;
number of subnets with which the ACL is associated.
Here you can:
modify ACL name (Name tag);
The Inbound rules tab displays a table with details of inbound rules:
rule number;
protocol;
CIDR block of IP addresses from which access is allowed;
ports;
rule-triggered action.
Here you can add, modify or delete an inbound rule.
The Outbound rules tab displays a table with details of outbound rules:
rule number;
protocol;
CIDR block of IP addresses to which access is allowed;
ports;
rule-triggered action.
Here you can add, modify or delete an outbound rule.
The Subnets tab displays a table with details of subnets with which this ACL is associated:
subnet ID;
subnet name;
CIDR block of IP addresses;
whether it is a default subnet (Yes/No).
Here you can also associate an ACL with subnets.
In the Tags tab, you can view tags assigned to the ACL. Here you can also add, modify, and delete tags.