Tutorials
In this article:
Tutorials#
Interconnecting VPCs through a transit gateway#
To interconnect two or more VPCs or specific subnets in these VPCs, you can use a transit gateway. The following example shows how to interconnect two VPCs, vpc-1 and vpc-2, in the same project. If necessary, you can attach to the transit gateway VPCs from other projects (including those of other companies) by providing access to the gateway.
The general procedure is as follows:
set the routes in the default route table of the transit gateway to attached VPCs;
set the route in route table of each VPC through the transit gateway to another VPC;
allow appropriate traffic, such as ICMP, in the security groups associated with the instances between which this traffic is to be transmitted.
Create a transit gateway#
Go to Interconnect Transit gateways and open the subsection of the same name.
Click Create.
Leave the Set route table as default option enabled. When it is selected, all new attachments are associated with the created default route table.
Click Create to create the gateway.
Create attachments#
Attachments must be created in each of the attached VPCs. (see about connecting transit gateways).
When creating the first attachment, you can specify subnets in one or more availability zones at will. However, when creating another attachment, you must specify subnets in the same availability zones as for the first one.
Traffic can be exchanged between any subnets in these VPCs, not only those directly attached to the transit gateway — it is only necessary to set routes through the transit gateway in the route tables of these subnets.
Note
Once created, the attachment cannot be associated with other subnets.
Go to Interconnect Transit gateways Attachments.
Click Create.
In the window that opens, set the following parameters:
The Name tag to identify the attachment, for example, vpc-1 (optionally).
The transit gateway you have created.
The VPC you want to connect.
VPC’s subnets to which the transit gateway will be attached.
Click Create to create the attachment.
A similar attachment must be created for another VPC.
Specify routes in the transit gateway route table#
The default route table of a transit gateway is created empty. For each attached VPC, you must specify a route to it through the transit gateway:
Go to Interconnect Transit gateways Route tables.
In the resource table, select the route table of the created transit gateway and click on the table ID to go to its page.
Open the Routes tab and click Add.
In the dialog window:
In the Network field, specify the network that corresponds to vpc-1 (you can specify the CIDR block of any existing subnet from vpc-1 if traffic must be forwarded to it).
Attachment to which vpc-1 is attached.
Click Create.
To set the route to vpc-2, repeat steps 3-5.
Specify routes in the VPC route table#
In each VPC, set a route to the transit gateway. Below it is assumed that in a VPC all subnets from which traffic must be routed to another VPC are associated with the main route table of that VPC. If a different route table is associated with some subnets, then for traffic to be transmitted from it to another VPC, a route via the transit gateway must also be set in it.
Go to Virtual machines Networking Route tables.
In the resource table, select the main route table of vpc-1 and click on the table ID to go to its page.
Open the Routes tab and click Add.
In the dialog window:
In the Network field, specify a target subnet in vpc-2. In this example, it is the same subnet in vpc-2 that you specified when creating the route in the transit gateway route table.
In the Gateway Type field, select Transit Gateway.
In the Gateway field, select the created transit gateway.
Click Add to create the route.
For vpc-2, repeat steps 2-4.
Enable required traffic#
For the traffic to flow between instances, enable the appropriate protocol in the security groups assigned to those instances.
As an example, lets say, you need to mutually ping instances in different VPCs. Here we assume that the default security group of a respective VPC is assigned to the instances.
Go to Virtual machines Security Security groups.
In the resource table, find the default security group for vpc-1 and click on its ID to go to the group page.
Open the Inbound Rules tab and click Add.
In the dialog window:
In the Protocol field, select ICMP.
For the Grant access option, select From network.
In the Network field, enter the subnet in vpc-2 that you specified when adding routes. The instance from vpc-2 must run in this subnet.
For vpc-2, repeat steps 2-4.
Check that everything is OK. From the instance in vpc-2, ping the instance in vpc-1 on its internal IP address. Do the same for the instance in vpc-1.
Traffic forwarding to a user gateway in another VPC#
If you need to forward traffic from one or more subnets in one VPC to a user gateway (for example, CheckPoint) in another VPC, you can do this through a transit gateway. The example shows how to route traffic to the Internet from a subnet in vpc-2 via a user gateway in vpc-1.
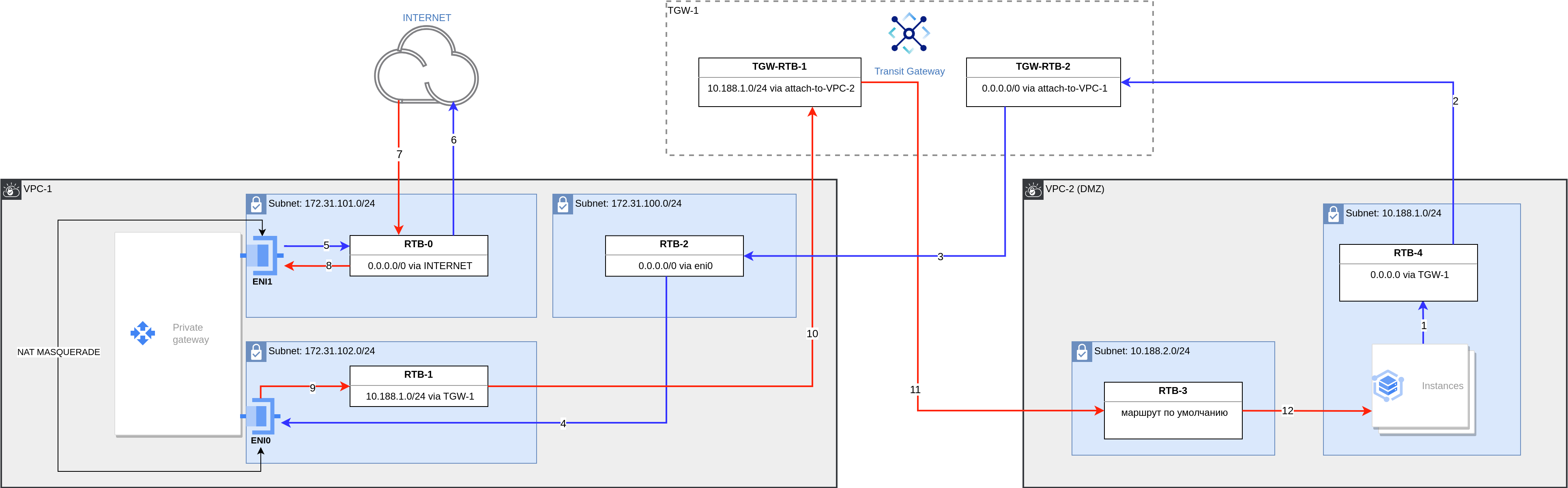
Traffic flow diagram:
Outbound traffic from the instances enters the 10.188.1.0/24 subnet associated with rtb-4.
Then, it is sent to the transit gateway attachment interface attach-to-vpc-2, where it is routed according to the transit gateway route table tgw-rtb-2.
Through the vpc-1 attachment, outbound traffic enters the 172.31.100.0/24 subnet and is routed according to the route table rtb-2 assigned to this subnet.
Traffic enters the eni0 interface. On the user gateway, with the help of NAT MASQUERADE or SNAT, traffic is forwarded to the eni1 interface in the 172.31.101.0/24 subnet.
Note
The route to 0.0.0.0/0 through 172.31.101.1 must be configured on the user gateway.
Through the eni1 interface, outbound traffic goes to a standard Internet gateway.
Then it goes to the Internet.
Return inbound traffic comes to the standard Internet gateway.
It is routed to the eni1 interface of the user gateway, where reverse NAT MASQUERADE or SNAT is performed.
Then traffic is forwarded to the eni0 interface and enters the 172.31.102.0/24 subnet.
Note
The route to vpc-2 through 172.31.102.1 must be configured on the user gateway.
Return traffic is sent to the transit gateway attachment interface attach-to-vpc-1 in accordance with rtb-1.
Traffic enters the transit gateway and is forwarded according to the transit gateway route table tgw-rtb-1 to vpc-2 attachment, from where it enters the 10.188.2.0/24 subnet.
In accordance with the route table rtb-3, traffic is forwarded to the instances.
The general procedure is as follows:
Create a transit gateway.
Create attachments in each VPC.
Create a transit gateway route table for each attachment.
In the transit gateway route tables, specify routes to the attached VPCs.
Specify routes in the subnet route tables.
Enable respective traffic in the security groups assigned to the user gateway and the instances sending traffic through that gateway.
Configure the user gateway.
Create a transit gateway#
Go to the Transit gateways section and open the corresponding subsection.
Click Create.
Disable Set route table as default option. When it is enabled, the created default route table of the transit gateway is assigned to all new attachments. In our case, it is not required, since we’ll create transit gateway route tables at the next step.
Click Create to create the gateway.
Create attachments#
Attachments must be created in each of the attached VPCs. (see about connecting transit gateways).
When creating the first attachment, you can specify subnets in one or more availability zones as you wish. However, when creating subsequent attachments, you must specify subnets in the same availability zones as for the first one. To create attachments, it is better to use separate subnets with a small CIDR block size, for example /28.
In any case, traffic can be transmitted between any subnets in these VPCs, not only those directly attached to the transit gateway. All you need is specify routes through the transit gateway, in the route tables associated with these subnets.
Note
Once created, the attachment cannot be associated with other subnets and availability zones cannot be changed.
Note
In our example, the following attachments are used:
attach-to-vpc-1 to vpc-1 (172.31.100.0/24);
attach-to-vpc-2 to vpc-2 (10.188.2.0/24).
Create a transit gateway route table for each attachment#
Note
In this section, route tables mean the transit gateway route tables.
Go to the Transit gateways section and open the Route tables section.
Click Create.
Enter a table name (for example, such name may match the VPC to which belongs the attachment that will use this route table).
To complete the route table creation, click Create.
Select the created route table, click Create associations and select the attachment to this VPC from the list.
Click Create to associate the attachment with the route table.
Repeat the steps for the second route table and second attachment.
Note
In our example, the following route tables are used:
tgw-rtb-1 for attachment attach-to-vpc-1;
tgw-rtb-2 for attachment attach-to-vpc-2.
Specify routes to the attached VPCs in the transit gateway route tables#
Transit gateway route tables are created empty. You must specify a route to another VPC in the route table associated with the attachment to that VPC. This should be done for each attached VPC.
Go to the Transit gateways section Route tables.
In the resource table, select the transit gateway route table, which is associated with the corresponding attachment of the created transit gateway (tgw-rtb-2). Click on the table ID to go to its page.
Open the Routes tab and click Add.
In the dialog window:
In the Network field, specify network 0.0.0.0/0 (all outbound traffic is forwarded).
Select the attachment to which vpc-1 is attached (attach-to-vpc-1).
Click Create.
Follow these steps to specify a route to vpc-2 (the route table tgw-rtb-1). In the Network field, specify the subnet in vpc-2, from which traffic is forwarded to the user gateway (10.188.1.0/24). Select the attachment to which vpc-2 is attached (attach-to-vpc-2).
Note
If traffic that goes through the user gateway comes from different vpc-2 subnets, then specify either routes to each of them or one route to the entire CIDR block corresponding to vpc-2.
Specify routes in the subnet route tables#
In each VPC, specify a route to the transit gateway. In order for traffic to be forwarded from a subnet to another VPC, the associated route table must also contain a route through the transit gateway.
Configure the rtb-4 route table for vpc-2:
Go to the Route Tables section.
In the resource table, select the rtb-4 route table of the required subnet (10.188.1.0/24) in vpc-2 and click on the table ID to go to its page.
Open the Routes tab and click Add.
In the dialog window:
In the Network field, specify the target subnet (0.0.0.0/0). In this example, this is the same subnet that you specified when creating the route in the transit gateway route table tgw-rtb-2.
In the Gateway Type field, select Transit Gateway.
In the Gateway field, select the created transit gateway (tgw-1).
Click Add to create the route.
Note
It is assumed that the attachment to vpc-2 (attach-to-vpc-2) is in the other vpc-2 subnet whose traffic is not forwarded through the user gateway.
Configure route tables rtb-0, rtb-1, and rtb-2 for vpc-1:
Go to the Route Tables section.
In the resource table, select rtb-2 route table associated with the 172.31.100.0/24 subnet and click on the table ID to go to its page. (The 172.31.100.0/24 subnet contains the transit gateway attachment interface.)
Open the Routes tab and click Add.
In the dialog window:
In the Network field, specify the target subnet (0.0.0.0/0).
In the Gateway type field, select Network interface.
In the Gateway field, select the “internal” interface (eni0) of your gateway.
Click Add to create the route.
In the resource table, select the rtb-1 route table associated with the 172.31.102.0/24 subnet and click on the table ID to go to its page. (The 172.31.102.0/24 subnet contains the “internal” interface eni0 of the user gateway.)
Go to the Routes tab and click Add.
In the dialog window:
In the Network field, specify the target subnet (10.188.1.0/24) in vpc-2 from which traffic is sent to the Internet.
Note
If traffic that goes through the user gateway comes from different vpc-2 subnets, then specify either routes to each of them or one route to the entire CIDR block corresponding to vpc-2.
In the Gateway Type field, select Transit Gateway.
In the Gateway field, select the created transit gateway (tgw-1).
Click Add to create the route.
In the resource table, select the rtb-0 route table associated with the 172.31.101.0/24 subnet and click on the table ID to go to its page. (The 172.31.101.0/24 subnet contains the “external” interface eni1 of the user gateway.)
In the dialog window:
In the Network field, specify the target subnet (0.0.0.0/0).
In the Gateway Type field, select Standard Internet Gateway.
Click Add to create the route.
Note
For traffic exchange between instances and the user gateway, enable the appropriate protocol in the security groups assigned to the user gateway and those instances.
Configure the user gateway#
For user gateway interfaces, disable the source/destination check.
Configure traffic forwarding from eni0 to eni1.
Configure NAT MASQUERADE or SNAT on the eni1 interface.